Trade does not happen without trust.
The geographically dispersed nature of international trade creates inherent difficulties when it comes to trusting a counterparty that may be located on the opposite end of the world.
Despite this inherent challenge, trade has continued to flow thanks to the development of robust systems, developed over hundreds of years, that injects the necessary element of trust.
It is self-evident to most that this is true for the physical and financial flows involved in a transaction. Buyers and sellers need to be confident that their goods and money will arrive – but the need for trust also extends to the data flows of a transaction.
From customs information on a certificate of origin, to safety information on a compliance certificate, the data that travels in tandem with the physical and financial flows is equally critical.
A trader that cannot trust this information may be dissuaded from participating in the trade since this information can become subject to later reference, scrutiny, and litigation down the line.
The global systems of trust that exist and facilitate trade today, however, are largely based on paper and other analogue methods, slowing the industry’s technological progress.
Progress towards trade digitalisation as a whole, which is widely touted as being a major boon to industry efficiency, will continually be anchored to the state of the industry’s digital trust mechanisms.
Trusted Technology Environment Working Group
The International Chamber of Commerce (ICC) Digital Standards Initiative’s (DSI) Industry Advisory Board’s Trusted Technology Environment (TTE) working group has released a report examining how to create and maintain this trusted technological environment.
In the report, the working group highlights the four key layers of a supply chain: the physical, financial, information, and trust layers.
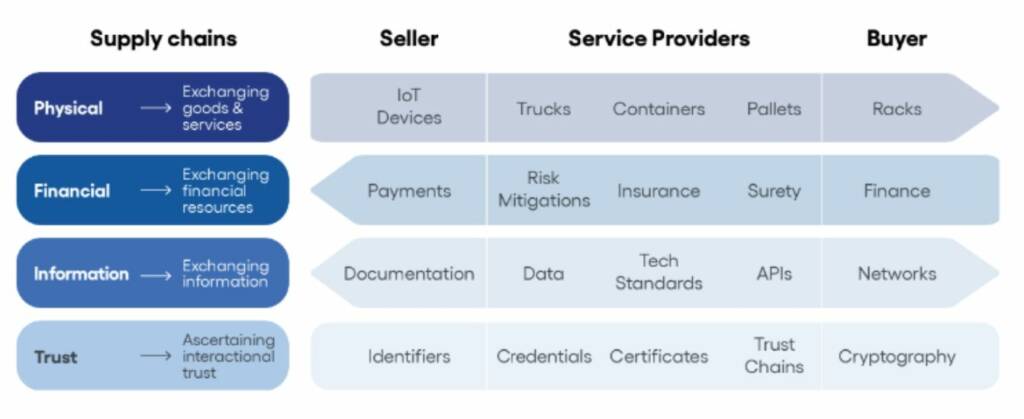
The report examines some of the proposed technological and cryptographic mechanisms used to establish and monitor trust on a digital level.
The frameworks range from the use of zero-trust architecture – which is backed by cryptographically produced verifiability – to the use of digital identities for all transacting parties.
Regardless of the specific methodologies used for a given example, the report emphasises the need for technology interoperability to allow these trusted data elements to flow seamlessly from one party to another.
Interoperability is key
International trade is a broad industry encompassing a collection of distinct actors – from traders and financiers to shipping carriers – each operating using their own technological systems.
To derive its full value, a trade asset like a letter of credit that is created in one system needs to be able to pass through multiple other systems before it reached its final destination.
At this final destination, the data contained needs to be verified against that initially created instance to ensure that it has not been altered somehow.
For this to happen, all of the systems involved need to be able to communicate using some form of a common language.
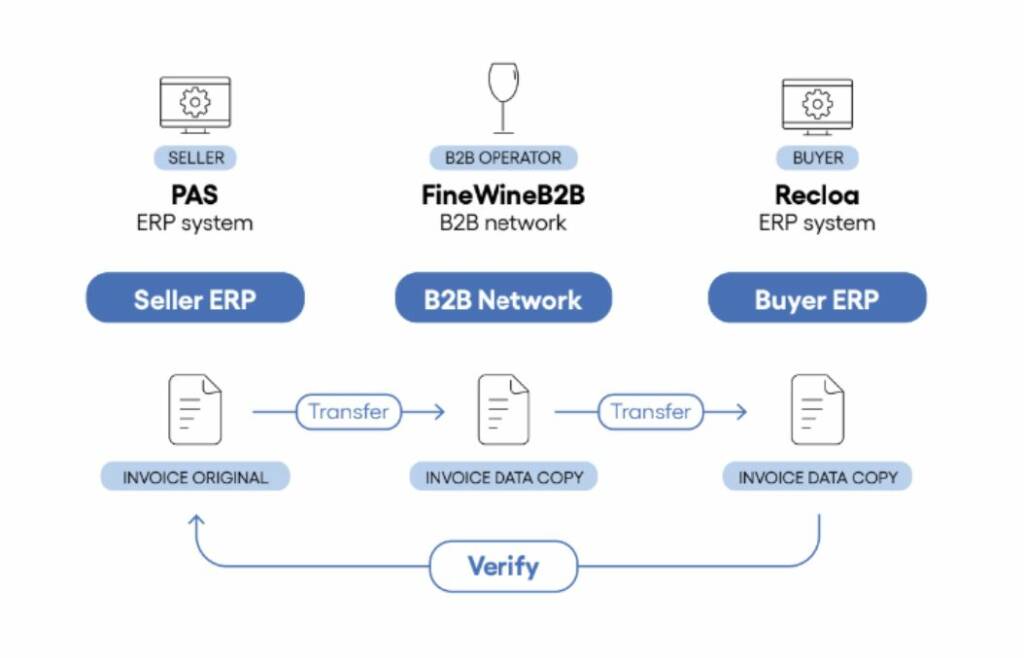
Digital systems created in isolation can quickly become silos or islands, or sunk investments, if systems and software instances are not interoperable.
This interoperability needs to encompass all aspects of the digital ecosystem, including the technical infrastructure layer, the data layer, the service layer, and, ultimately, the legal layer.
The concept of zero-trust
The traditional mode of operating applications within an organisational intranet has been through firewalls, role-based access limitations, and directory services.
This security structure, however, has generally seeped beyond individual organisations and can also be implemented when dealing with externally operated applications with those of external service providers.
This approach, however, has led to a series of security concerns, particularly when dealing with third parties who operate their own cybersecurity practices, often beyond the control of the organisation sharing the data.
To mitigate these issues, many companies now follow an environment based on zero-trust architecture.
Zero-trust architecture is based on verifiable credentials and addresses the exponential permutation growth in the number of services to be interconnected.
It does not pose vulnerabilities like phishing attacks, as access privileges are not centred around users but always around the resources used.
This way, zero-trust architectures and transitive trust support the right to use certain data for a certain process at a certain time but not for anything else or at a later point in time.
 Australia
Australia Hong Kong
Hong Kong Japan
Japan Singapore
Singapore United Arab Emirates
United Arab Emirates United States
United States France
France Germany
Germany Ireland
Ireland Netherlands
Netherlands United Kingdom
United Kingdom










Comments are closed.